Difference between revisions of "2166: Stack"
m (rv) |
|||
| Line 1: | Line 1: | ||
| − | + | {{comic | |
| + | | number = 2166 | ||
| + | | date = June 21, 2019 | ||
| + | | title = Stack | ||
| + | | image = stack.png | ||
| + | | titletext = Gotta feel kind of bad for nation-state hackers who spend years implanting and cultivating some hardware exploit, only to discover the entire target database is already exposed to anyone with a web browser. | ||
| + | }} | ||
| + | |||
| + | ==Explanation== | ||
| + | |||
| + | In software engineering, a {{w|Solution stack|tech stack}} is the set of technology platforms and tools that a company or app uses. A common tech stack is {{w|LAMP (software bundle)|LAMP}}, composed of a {{w|Linux}} {{w|Operating system|operating system}}, an {{w|Apache HTTP Server|Apache}} {{w|Web server}}, a {{w|MySQL}} {{w|database}}, and the {{w|PHP}} programming language. | ||
| + | |||
| + | In this instance, all of the layers represent systems which have been subverted or compromised ("hacked") by various entities, instead of various software technologies. The stack resembles an OSI network architecture, with an eighth layer added representing the user itself. | ||
| + | |||
| + | '''Compromised by a customer:''' The user experience, above the OSI layers. Compromised by users doing something wrong or ill-advised. | ||
| + | |||
| + | '''Compromised by a former employee:''' In the OSI model, this would be the application layer. The application may include a hidden spyware in its codebase. Recent examples of compromise: Desjardins Group | ||
| + | |||
| + | '''Compromised by a current employee:''' This is the presentation layer. See above. Probably, that was compromised by a mistake of a current unexperienced employee. | ||
| + | |||
| + | '''Compromised by Bitcoin miners:''' This is the session layer, where SSL historically resided. Cryptographic exploits may cause compromise of whole communication. Examples of compromise: Dozens of bitcoin mining viruses. | ||
| + | |||
| + | '''Compromised by unknown hackers:''' This is the transport layer. IP and port spoofing is a possible compromise. | ||
| + | |||
| + | '''Compromised by our own government:''' This is the network layer. It refers to communication intercepts by governments. Examples of compromise: Cisco (for US citizens) | ||
| + | |||
| + | '''Compromised by a foreign government:''' This is the data link layer. This layer may be compromised by malrouting packets. Examples of compromise: Huawei (for non-Chinese citizens) | ||
| + | |||
| + | '''Massive undiscovered hardware vulnerability:''' This is the physical layer. An undiscovered hardware vulnerability may cause compromises further up in the stack. Examples of compromises: | ||
| + | {{w|Intel Management Engine}}, {{w|Meltdown (security vulnerability)|Meltdown}} | ||
| + | |||
| + | In the title text, Randall expresses sympathy for a situation where someone spends a significant length of time on something that then becomes completely unnecessary. In this case, it's the state-sponsored hackers who develop an exploit of some hardware component, which then becomes completely useless because the target database on that hardware is totally open anyway to anyone with a web browser (which is essentially everyone). While he's not suggesting he agrees with their hacking, he has some sympathy for their wasted effort. | ||
| + | |||
| + | ==Transcript== | ||
| + | :[Single-panel with a label at the top and 8 box layers stacked vertically, with in and out arrows at the top representing normal data flow and an arrow out of each box to the left or right representing exploit data flow] | ||
| + | :The Modern Tech Stack | ||
| + | :*Compromised by a customer (arrow to the right) | ||
| + | :*Compromised by a former employee (arrow to the left) | ||
| + | :*Compromised by a current employee (arrow to the right) | ||
| + | :*Compromised by bitcoin miners (arrow to the right) | ||
| + | :*Compromised by unknown hackers (arrow to the left) | ||
| + | :*Compromised by our own government (arrow to the right) | ||
| + | :*Compromised by a foreign government (arrow to the left) | ||
| + | :*Massive undiscovered hardware vulnerability (arrow to the right) | ||
| + | |||
| + | ==Trivia== | ||
| + | Comic [[1636: XKCD Stack]] also has a hypothetical technology stack, with farcical layers. | ||
| + | |||
| + | {{comic discussion}} | ||
| + | |||
| + | [[Category:Computers]] | ||
| + | [[Category:Programming]] | ||
Revision as of 22:31, 4 May 2022
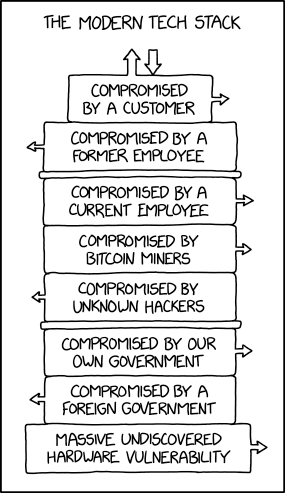
Explanation
In software engineering, a tech stack is the set of technology platforms and tools that a company or app uses. A common tech stack is LAMP, composed of a Linux operating system, an Apache Web server, a MySQL database, and the PHP programming language.
In this instance, all of the layers represent systems which have been subverted or compromised ("hacked") by various entities, instead of various software technologies. The stack resembles an OSI network architecture, with an eighth layer added representing the user itself.
Compromised by a customer: The user experience, above the OSI layers. Compromised by users doing something wrong or ill-advised.
Compromised by a former employee: In the OSI model, this would be the application layer. The application may include a hidden spyware in its codebase. Recent examples of compromise: Desjardins Group
Compromised by a current employee: This is the presentation layer. See above. Probably, that was compromised by a mistake of a current unexperienced employee.
Compromised by Bitcoin miners: This is the session layer, where SSL historically resided. Cryptographic exploits may cause compromise of whole communication. Examples of compromise: Dozens of bitcoin mining viruses.
Compromised by unknown hackers: This is the transport layer. IP and port spoofing is a possible compromise.
Compromised by our own government: This is the network layer. It refers to communication intercepts by governments. Examples of compromise: Cisco (for US citizens)
Compromised by a foreign government: This is the data link layer. This layer may be compromised by malrouting packets. Examples of compromise: Huawei (for non-Chinese citizens)
Massive undiscovered hardware vulnerability: This is the physical layer. An undiscovered hardware vulnerability may cause compromises further up in the stack. Examples of compromises: Intel Management Engine, Meltdown
In the title text, Randall expresses sympathy for a situation where someone spends a significant length of time on something that then becomes completely unnecessary. In this case, it's the state-sponsored hackers who develop an exploit of some hardware component, which then becomes completely useless because the target database on that hardware is totally open anyway to anyone with a web browser (which is essentially everyone). While he's not suggesting he agrees with their hacking, he has some sympathy for their wasted effort.
Transcript
- [Single-panel with a label at the top and 8 box layers stacked vertically, with in and out arrows at the top representing normal data flow and an arrow out of each box to the left or right representing exploit data flow]
- The Modern Tech Stack
- Compromised by a customer (arrow to the right)
- Compromised by a former employee (arrow to the left)
- Compromised by a current employee (arrow to the right)
- Compromised by bitcoin miners (arrow to the right)
- Compromised by unknown hackers (arrow to the left)
- Compromised by our own government (arrow to the right)
- Compromised by a foreign government (arrow to the left)
- Massive undiscovered hardware vulnerability (arrow to the right)
Trivia
Comic 1636: XKCD Stack also has a hypothetical technology stack, with farcical layers.
Discussion
I wasn't sure how to format the transcript, but I put in something for starters - feel free to adjust as needed. I don't think the arrow directions for each layer are significant and are just random. Ianrbibtitlht (talk) 14:53, 21 June 2019 (UTC)
Is there any significance to the two thin layers inserted between the larger labels in the stack? I don't think so, but I'm not sure either way! Ianrbibtitlht (talk) 15:08, 21 June 2019 (UTC)
- I would say that the thin layers are actually boundaries between major parts of the stack. The lower one seems to be a boundary between hardware/firmware and (system & application) software, the upper one a boundary between a software product/system/framework as released/sold and the same system as installed/configured at a particular site (the "customer" layer suggests that to me) -- Malgond (talk) 16:17, 21 June 2019 (UTC)
- I was thinking something along those lines, but I thought it was strange there was one inserted between the compromises by a current and a past employee. (A compromise by a past employee was likely implemented while they were employed, maybe as a backdoor they can access after leaving the company.) Ianrbibtitlht (talk) 17:34, 21 June 2019 (UTC)
- I think this stack is most supposed to be some form of website. The customer (a site visitor/user) is exploiting a Javascript vulnerability. The former employee is exploiting a deeper vulnerability but still through the browser/otherwise through the web (e.g. an URL-based exploit, like adding "/../"s to url to access files that aren't supposed to be part of the site) that they know about because they worked on it. The current employee is compromising using their access to the code, the database, or the server, hence the division. Schpeelah (talk) 17:58, 21 June 2019 (UTC)
- I agree that the stack likely represents a website (maybe all websites), and your point about the top two using only the browser being the reason for the separation bar makes perfect sense! Thanks for sharing your thoughts. Ianrbibtitlht (talk) 18:35, 21 June 2019 (UTC)
- I think this stack is most supposed to be some form of website. The customer (a site visitor/user) is exploiting a Javascript vulnerability. The former employee is exploiting a deeper vulnerability but still through the browser/otherwise through the web (e.g. an URL-based exploit, like adding "/../"s to url to access files that aren't supposed to be part of the site) that they know about because they worked on it. The current employee is compromising using their access to the code, the database, or the server, hence the division. Schpeelah (talk) 17:58, 21 June 2019 (UTC)
- I was thinking something along those lines, but I thought it was strange there was one inserted between the compromises by a current and a past employee. (A compromise by a past employee was likely implemented while they were employed, maybe as a backdoor they can access after leaving the company.) Ianrbibtitlht (talk) 17:34, 21 June 2019 (UTC)
Not to be confused with the XKCD Stack. --162.158.182.232 15:52, 21 June 2019 (UTC)
Isn't the title text a reference to when china had some surveillance databases publicly visible? Rerere284 (talk) 17:48, 21 June 2019 (UTC)
we seem to be missing compromised by anti virus software - but that aside I want the t-shirt162.158.34.206
- It's probably not a Windows-based server, so no anti-virus software is needed! Ianrbibtitlht (talk) 23:44, 21 June 2019 (UTC)
I think the stack resembles an 8-layer wedding cake! Ianrbibtitlht (talk) 02:24, 22 June 2019 (UTC)
I don't think labeling the layers by the OSI layers makes much sense. There is no indication in the comic that the OSI model is intended. If going to cover OSI, maybe put in a table with the OSI model levels as one column (to clearly separate that interpretation from others). 162.158.107.79 08:00, 23 June 2019 (UTC)
- I disagree. There's a clear link, with hardware exploits on the bottom, and the "foreign government" layer is likely a reference to the US-Huawei situation. 172.68.141.52 13:01, 24 June 2019 (UTC)
- It is not so clear. First of all there's no mention of OSI; moreover there's eight layers in the picture, not seven. "Foreign government" may still be at ISO Layer 1, e.g. at a chip fab, or somewhere higher such as in factory-installed firmware or OS image. "Own government" may be anything starting from installing hardware implants via interdiction, through firmware/OS/crypto compromise (planted vulnerabilities), 0-days (discovered vulnerabilities) to traffic capture/analysis - and so on. My personal take on layers' meanings is: HW design shortcomings; malicious firmware installed at foreign factories; NSA-planted APTs (low-level); malware infections; Javascript (or trojan app) mining code; backdoors planted in app code by a current employee; vulnerabilities in app code exploited by a former employee; user-inflicted problems such as misconfiguration or installation of questionable software -- Malgond (talk) 17:51, 24 June 2019 (UTC).
- This is where I'm at on the question as well. It seems that connecting each tech stack layer to an OSI model layer is a too bit restrictive. Ianrbibtitlht (talk) 18:35, 24 June 2019 (UTC)
- Just wanted to add my thoughts, but I saw the eighth "user layer" as representing the human element, e.g. social engineering, and the fact its narrower than the other layers might indicate its supposed to not be standard. In my mind, this would make sense as most companies have a support desk that doesn't realise its own role in security, and can therefore be compromised by a customer with little technical skill. Maybe I'm clutching at straws to fit in in with the OSI model, but what other model is there that's well known enough? 162.158.158.149 05:25, 4 July 2019 (UTC)
- This is where I'm at on the question as well. It seems that connecting each tech stack layer to an OSI model layer is a too bit restrictive. Ianrbibtitlht (talk) 18:35, 24 June 2019 (UTC)
- It is not so clear. First of all there's no mention of OSI; moreover there's eight layers in the picture, not seven. "Foreign government" may still be at ISO Layer 1, e.g. at a chip fab, or somewhere higher such as in factory-installed firmware or OS image. "Own government" may be anything starting from installing hardware implants via interdiction, through firmware/OS/crypto compromise (planted vulnerabilities), 0-days (discovered vulnerabilities) to traffic capture/analysis - and so on. My personal take on layers' meanings is: HW design shortcomings; malicious firmware installed at foreign factories; NSA-planted APTs (low-level); malware infections; Javascript (or trojan app) mining code; backdoors planted in app code by a current employee; vulnerabilities in app code exploited by a former employee; user-inflicted problems such as misconfiguration or installation of questionable software -- Malgond (talk) 17:51, 24 June 2019 (UTC).