Difference between revisions of "416: Zealous Autoconfig"
(In this comic...) |
(→Explanation: The Lenhart children have both a father and a mother (as implied by the word parents)) |
||
| Line 12: | Line 12: | ||
The laptop's Wi-Fi autoconfig utility, instead of requesting a password, first attempts using "common" passwords (known as a {{w|Dictionary attack|dictionary attack}}). Failing this, it attempts to exploit a {{w|Wired Equivalent Privacy|WEP}} vulnerability, which surprises Cueball. This also fails, possibly because Miss Lenhart used {{w|Wi-Fi Protected Access|WPA}} instead of WEP. | The laptop's Wi-Fi autoconfig utility, instead of requesting a password, first attempts using "common" passwords (known as a {{w|Dictionary attack|dictionary attack}}). Failing this, it attempts to exploit a {{w|Wired Equivalent Privacy|WEP}} vulnerability, which surprises Cueball. This also fails, possibly because Miss Lenhart used {{w|Wi-Fi Protected Access|WPA}} instead of WEP. | ||
| − | In the third panel, the autoconfig then connects to Cueball's Bluetooth phone and uses it to call a local school and finds that | + | In the third panel, the autoconfig then connects to Cueball's Bluetooth phone and uses it to call a local school and finds that the Lenhart children are attending. |
| − | In the fourth panel, the autoconfig notifies "field agents" to kidnap | + | In the fourth panel, the autoconfig notifies "field agents" to kidnap the Lenhart children, then starts "negotiating" with their parents. Cueball, frightened by these actions, repeatedly presses Ctrl-C in an attempt to cancel the process, with little success. Ctrl+C is used to abort programs started from a terminal (Unix/Linux) or a command line prompt (cmd.exe under Windows). Part of the humor is that he only attempts to cancel quite late in the process, well after (for instance) the school was first called. |
The title text mentions {{w|Ubuntu}}, a Linux distribution that attempts to be as user friendly as possible. | The title text mentions {{w|Ubuntu}}, a Linux distribution that attempts to be as user friendly as possible. | ||
Revision as of 02:22, 14 October 2013
| Zealous Autoconfig |
 Title text: I hear this is an option in the latest Ubuntu release. |
Explanation
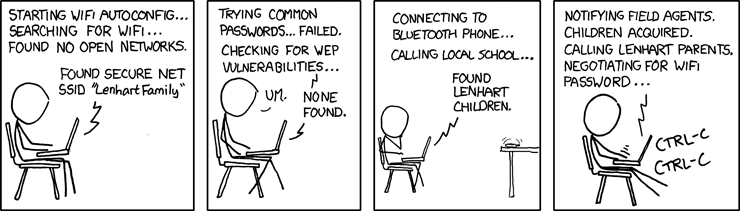
Cueball is seen attempting to connect his laptop to a Wi-Fi network. He manages to find a secure access point named "Lenhart Family" (which is pesumably Miss Lenhart's home Wi-Fi access point) and attempts to connect to it.
The laptop's Wi-Fi autoconfig utility, instead of requesting a password, first attempts using "common" passwords (known as a dictionary attack). Failing this, it attempts to exploit a WEP vulnerability, which surprises Cueball. This also fails, possibly because Miss Lenhart used WPA instead of WEP.
In the third panel, the autoconfig then connects to Cueball's Bluetooth phone and uses it to call a local school and finds that the Lenhart children are attending.
In the fourth panel, the autoconfig notifies "field agents" to kidnap the Lenhart children, then starts "negotiating" with their parents. Cueball, frightened by these actions, repeatedly presses Ctrl-C in an attempt to cancel the process, with little success. Ctrl+C is used to abort programs started from a terminal (Unix/Linux) or a command line prompt (cmd.exe under Windows). Part of the humor is that he only attempts to cancel quite late in the process, well after (for instance) the school was first called.
The title text mentions Ubuntu, a Linux distribution that attempts to be as user friendly as possible.
Transcript
- [Cueball sitting on a chair with his laptop in his lap.]
- Laptop: Starting WiFi autoconfig... searching for WiFi... Found no open networks.
- Laptop: Found secure net SSID "Lenhart Family"
- Laptop: Trying common passwords... Failed. Checking for WEP Vulnerabilities...
- Cueball: Um.
- Laptop: None found.
- [Cueball still sitting with laptop in his lap, but hand is on chin. Phone on table across room starts vibrating.]
- Laptop: Connecting to Bluetooth phone... Calling local school... Found Lenhart children.
- [Cueball furiously typing on his laptop.]
- Laptop: Notifying field agents. Children acquired. Calling Lenhart parents. Negotiating for WiFi password...
Discussion
I have my network autoconfig set up to run a rainbow table attack if there's a password on the network. Wifi everywhere is great. Davidy22(talk) 15:05, 1 November 2012 (UTC)
- That's superb! Suspender guy (talk) 17:12, 22 December 2015 (UTC)
- Do you have that rainbow table somewhere? Wifi everywhere is great. PoolloverNathan[talk]U•T•S•c 17:59, 24 April 2023 (UTC)
But how would the school know about the Lenhart children if Mrs. Roberts deleted the students table? 184.11.73.88 (talk) (please sign your comments with ~~~~)}
- I say it'd be a liveware attack. A voice-call from the application, with in-built speech-synthisis and speech-recognition capabilities, requesting information from the school secretary him/herself. Probably a Black Hat construction. Or Hartigan (/whoever) from the Leverage series... ;) 178.107.249.215 23:43, 17 June 2013 (UTC)
I think Miss Lenhart must be the Lenhart children's paternal aunt. Their mother is most probably Mrs. Lenhart. Xhfz (talk) 02:20, 14 October 2013 (UTC)
When I saw "Ctrl + C" my first thought was "copy." It's the dumb thing about windows and every implementation that uses that. 108.162.245.217 14:02, 9 July 2014 (UTC)
It gets worse! I regularly use Konsole, where ctrl-c cancels things; ctrl-shift-c copies, but then I start using ctrl-shift-c in Chrome and end up debugging web pages instead of copying text. GAH! 141.101.70.157 (talk) (please sign your comments with ~~~~)
huh i once was playing kol clicked something and ended up with tons of php in my screen An user who has no account yet (talk) 17:41, 6 September 2023 (UTC)
A similar concept to 538: Security. Shanek (talk) 12:29, 1 May 2015 (UTC)
Believe it or not, you can use ctrl-insert to copy on almost any linux or windows program. Shift-delete is cut and shift-insert is paste. --PsyMar (talk) 13:13, 1 May 2015 (UTC)
- I think the difference is WordPerfect vs Word short-cuts, both are supported both for historic reason and to support both left and right handed users with a mouse in their primary hand.162.158.133.114 01:45, 23 December 2015 (UTC)
- XKCD 1479 right here.108.162.237.124 17:49, 9 May 2015 (UTC)
I think there's also a pun on "acquired". A network address can be acquired, but when children are acquired it means something quite different. (However, in context they are both required to connect.) 198.41.238.32 11:22, 27 November 2015 (UTC)
