1200: Authorization
Explanation[edit]
Certain computer operating systems were initially designed as multi-user systems. As the name suggests, these systems are meant to be used by multiple people or users, sometimes at the same time. To prevent malicious or accidental destructive damage to the system, users are split into two general groups: regular users, and system administrators (or admins). Regular users can access and use programs on the computer, but only the admin is allowed to make changes to how the computer runs. This same split level of security continues to this day, even in privately owned, or "home", computers.
The wry remark made here is that in the decades since the most important things on a computer to be worried about are no longer the programs that it runs, but the private personal data it contains and can access (usually online). Anyone who wished to do real mischief on an active computer could do considerable damage without ever caring what the admin password was. The admin password, in effect, now protects something that has become barely, if any, concern.
This comic pokes fun at the authorization mechanisms surrounding most operating systems' administrator accounts. It makes the argument that the user's data is more valuable than the integrity of the system. This is arguably true for most personal systems, although it is probably not true in a shared-server setup, where a system compromise could lead to the exposure of many users' data.
Essentially, once a user is logged in, they can typically access all of their data without any further restriction. Modifying the operating system (for example, to install drivers) requires a separate password.
In fact, this password protection also hinders installation of malware, which is otherwise possible even remotely, with the malware then being able to e.g. steal passwords, enabling a cracker anywhere in the world to access your accounts without ever needing to touch your computer. So having your computer set up to not to ask you for an administrator's password arguably implies a bigger risk of identity theft than allowing others to access your system physically while being logged in does.
The title text alludes to the security practice where computers automatically lock the user out after a few minutes, requiring a password from the user in order to continue using it. Instead, Randall's computer automatically switches to his brother's account, presumably compromising his data instead of Randall's. The fact that Randall's brother has an account on Randall's computer even though Randall does not live with his childhood family (so his brother would not need to use his computer often) could be because Randall does not want his brother to be able to access his files, PayPal, etc… when he uses his computer, which would indicate that either Randall is cynical, his brother is not trustworthy, or Randall is simply following the principle of least privilege.
Transcript[edit]
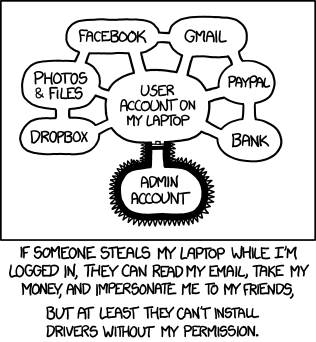
- [Diagram showing several connected bubbles. One in the center says "User account on my laptop," surrounded by "Dropbox," "Photos & files," "Facebook," "Gmail," "PayPal," and "Bank," which are connected to the middle bubbles and to each other. Below the middle bubble is one labeled "Admin account," which is covered in spikes, and has a "door" to the bubble above it.]
- If someone steals my laptop while I'm logged in, they can read my email, take my money, and impersonate me to my friends, but at least they can't install drivers without my permission.
Discussion
I find it funny at first because I thought Randall hates his brother, so he set it to switch to his brothers to let other people hack randall's BROTHER's account instead of his. XkcdIsGood (talk) 16:47, 20 March 2022 (UTC)
This is the reason that I set sudo to not prompt for a password. I just make sure my computer locks itself aggressively. 130.18.105.246 06:59, 17 April 2013 (UTC)
The admin account should still be guarded EXACTLY for the ability to install drivers. The driver you don't want to have installed is keylogger stealing your passwords. I mean, you don't have your bank password remembered in browser, do you? Still, auto-logout or auto-lock is important feature. You should also set-up and use separate account for high-risk activities (like opening emails from unknown persons promising naked celebrities ... ok, you actually shouldn't be opening such emails at all, but if you are really curious ...). -- Hkmaly (talk) 09:06, 17 April 2013 (UTC)
- Even if you can log into your bank account, you could not transfer money without authorizing transactions. BKA (talk) 11:23, 17 April 2013 (UTC)
- My bank account website logs me out if I'm inactive for 10 minutes. It doesn't even leave the page up, it switches to a login screen. 24.77.229.71 14:35, 17 April 2013 (UTC)
- I wonder how useful a keylogger would be if you never typed a username or e-mail to go with the password. Every important account I have has that remembered, and I just type the password. It sounds like it would be zero context. 76.106.251.87 15:09, 17 April 2013 (UTC)
- Except usernames tend to be reasonably easy to figure. E-mails certainly are what with folks tending to broadcast their e-mail addresses to everyone. So passwords, although also often not overly difficult to crack (http://xkcd.com/936/), remain the part not generally known. Not worrying about a keylogger picking up a password, even "out of context" would be a mistake. 67.51.59.66 17:11, 17 April 2013 (UTC)
Actually, for many years popular operating systems such as MS Windows did *not* have separate security for system administration, which made it very popular for the propagation of viruses and other malware. And once it was introduced, it wasn't enforced for many years. Only relatively recently this is happening, and still viruses, trojan horses and botnets thrive, because it is slightly inconvenient for the user to act safe(r). 213.84.74.36 13:13, 19 April 2013 (UTC)
Not agree with Randall on this one. Laptop stealing is very physical, there are way to keep people from physically able to use our active login session, such as make sure the laptop is physically secured when possible, make sure the screen locked out when we are away (we can automate that using bluetooth detection), etc. Root password protect another kind of attack, generally more clandestine one, such as trojan and rootkit installations, which can be more dangerous as we may not be aware it is there. Arifsaha (talk) 17:06, 6 May 2013 (UTC)
Not going to agree. I use lastpass for passwords, have every (important) site protected with 2fac, and firefox wipe all my userdata everytime I close it, so even if a keylogger is installed, or they have physical access to my device, they can't get to my personal information. So that covers Facebook, Gmail, Paypal, and the Bank. Everything else is encrypted