Difference between revisions of "1966: Smart Home Security"
m (rv) |
(→Explanation) |
||
| (26 intermediate revisions by 12 users not shown) | |||
| Line 11: | Line 11: | ||
With the proliferation of smart appliances in recent years, there is a growing trend of hackers taking over smart "Internet of Things" devices and adding them to {{w|botnets}}. The hardware is then used for DDOS attacks, crypto mining etc. The "{{w|Mirai (malware)|Mirai}}" botnet, for example, made of over 500,000 compromised routers, refrigerators, TVs, DVRs, baby monitors, thermostats, and webcams, was used in October 2016 to take down DynDNS, one of the core infrastructure providers for the internet in North America. | With the proliferation of smart appliances in recent years, there is a growing trend of hackers taking over smart "Internet of Things" devices and adding them to {{w|botnets}}. The hardware is then used for DDOS attacks, crypto mining etc. The "{{w|Mirai (malware)|Mirai}}" botnet, for example, made of over 500,000 compromised routers, refrigerators, TVs, DVRs, baby monitors, thermostats, and webcams, was used in October 2016 to take down DynDNS, one of the core infrastructure providers for the internet in North America. | ||
| − | With the constant potential threat, security updates must be constantly published, and vulnerabilities must be found by the original developers and "{{w|White hat (computer security)|white hat}}" hackers (the faceless team of engineers [[Randall]] describes), before they are found and exploited by "{{w|black hat}}" hackers. At any time, these defenders could step down from their jobs, leaving devices defenseless. | + | With the constant potential threat, security updates must be constantly published, and vulnerabilities must be found by the original developers and "{{w|White hat (computer security)|white hat}}" hackers (the faceless team of engineers [[Randall]] describes), before they are found and exploited by "{{w|black hat}}" hackers (not to be confused with [[Black Hat]]). At any time, these defenders could step down from their jobs, leaving devices defenseless. |
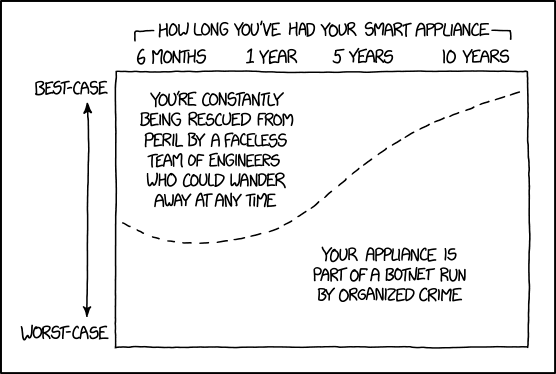
The graph shows the various cases of how well things go on the y-axis, compared to how long it has been owned on the x-axis. The probability of compromise briefly dips (indicative of first rounds of security fix updates & the time window when you can easily exchange the product if you find out it's faulty) within the 1st year, then rises: the older a device/software is, the less likely it is to consistently receive security updates for protection, so they are more likely to be hacked, even in the best case. After 10 years, the device/software is most likely outdated and is not being used anymore. Companies then no longer find it profitable to continually update the product. Thus, they pull the support out, even if people are still using the device, leaving customers vulnerable. | The graph shows the various cases of how well things go on the y-axis, compared to how long it has been owned on the x-axis. The probability of compromise briefly dips (indicative of first rounds of security fix updates & the time window when you can easily exchange the product if you find out it's faulty) within the 1st year, then rises: the older a device/software is, the less likely it is to consistently receive security updates for protection, so they are more likely to be hacked, even in the best case. After 10 years, the device/software is most likely outdated and is not being used anymore. Companies then no longer find it profitable to continually update the product. Thus, they pull the support out, even if people are still using the device, leaving customers vulnerable. | ||
Latest revision as of 05:39, 9 January 2024
Explanation[edit]
With the proliferation of smart appliances in recent years, there is a growing trend of hackers taking over smart "Internet of Things" devices and adding them to botnets. The hardware is then used for DDOS attacks, crypto mining etc. The "Mirai" botnet, for example, made of over 500,000 compromised routers, refrigerators, TVs, DVRs, baby monitors, thermostats, and webcams, was used in October 2016 to take down DynDNS, one of the core infrastructure providers for the internet in North America.
With the constant potential threat, security updates must be constantly published, and vulnerabilities must be found by the original developers and "white hat" hackers (the faceless team of engineers Randall describes), before they are found and exploited by "black hat" hackers (not to be confused with Black Hat). At any time, these defenders could step down from their jobs, leaving devices defenseless.
The graph shows the various cases of how well things go on the y-axis, compared to how long it has been owned on the x-axis. The probability of compromise briefly dips (indicative of first rounds of security fix updates & the time window when you can easily exchange the product if you find out it's faulty) within the 1st year, then rises: the older a device/software is, the less likely it is to consistently receive security updates for protection, so they are more likely to be hacked, even in the best case. After 10 years, the device/software is most likely outdated and is not being used anymore. Companies then no longer find it profitable to continually update the product. Thus, they pull the support out, even if people are still using the device, leaving customers vulnerable.
The title text suggests that there may be some silver lining to having your device controlled by organized crime professionals: they have a vested interest in keeping your device working well enough that you keep it plugged in. So, the more organized, pragmatic attackers will actually secure it against competing attackers, especially those of a more prankster-like mindset, who would cause more noticeably malicious changes. Advanced malware in the wild does frequently block and evict competing malware, so Randall is probably right. Some IOT malware may thus provide "regular security update services" after the original manufacturers give up, some at a conceivably acceptable cost of a few cents' worth of electrical usage for a crypto-miner. However, it could very easily go horribly wrong, for instance if that miner is hiding by letting a refrigerator run 2°C higher than its outputs allege and using the energy difference to max out the processor on mining operations.
Transcript[edit]
- [A graph is shown inside a frame. There is one dotted line going from the middle of the left edge, then dipping slightly before rising slowly at first, then more rapid and finally slowing its ascend down as it nears the top right corner.]
- [Above the frame is the title of the x-axis, and from each end of this text, there is a small line going out and then down, to indicate a time range, which is shown below with four times:]
- How long you've had your smart appliance
- 6 months 1 year 5 years 10 years
- [Along the left part of the frame there runs a double arrow and at the top and bottom of these arrows there are legends at the top and bottom of the panels height:]
- Best-case
- Worst-case
- [Inside the panel there is text above the dotted line to the left, and below the dotted line to the right:]
- You're constantly being rescued from peril by a faceless team of engineers who could wander away at any time
- Your appliance is part of a botnet run by organized crime
Discussion
When I went to explainxkcd right after the comic posted, I saw this in the incomplete tag: "Created by ORGANIZED CRIME". Today is the day this website has officially swallowed its own tail. Djbrasier (talk) 15:50, 12 March 2018 (UTC)
- Oh no! We must eradicate this enemy- We must start violent purging- No one can be trusted! Linker (talk) 16:46, 12 March 2018 (UTC)
Hmm. Isn't the concern for smart appliances usually that since they're internet-connected, they can be used to for DDoS and other nefarious purposes? I mean, a smart thermostat doesn't really have the capability to spy on its owners, right?
- They can spy on your temperature preferences! (Dun dun dah!). You do have a point though. I originally was thinking more like smart home assistants, as that seems to be the craze now. That is ignoring the majority smart devices in the market though. You could get some information from most though, even it is minimal. You could get a rough floorplan from a roomba, you could get an idea what kind of products people buy with smart fridges... etc.Linker (talk) 11:29, 19 March 2018 (UTC)
- A smart thermostat often knows when you are home and not. It could easily be used to develop a pattern of behavior to determine when would be the best time to rob your house. Then there's smart door locks, with the obvious consequences of hacking. But yes, botnets are one of the biggest problems. Note that the graph (accurately!) shows a not-so-great best case on day 1, as most IoT security is awful.173.245.52.67 17:18, 12 March 2018 (UTC)
- Agreed. A much more likely scenario is that your device is being used for a botnet. Smart appliances aren't updated as reliably as personal computers (since they're "set and forget" devices), and the owner is less likely to notice if they've been hacked (because you won't notice if your thermostat is running a little slow), so they're a prime target for hackers. That's also why the graph shows the risk increases as time goes by - the manufacturer stops patching the device, but the hacker will keep trying to get in. --162.158.79.89 17:24, 12 March 2018 (UTC)
- The risk in a smart thermostat is not the information it sends, but the fact that it is connected to your network. If the security on the thermostat is weak, it provides a gateway to the rest of your network. Hack the thermostat and install malware that sits there silently trying password combinations to the rest of your devices. Rtanenbaum (talk) 13:32, 13 March 2018 (UTC)
- The risk of IOT devices is that they control physical objects and that can be used to do physical harm. A smart thermostat controlling an A/C or heat pump switch a multi-kilowatt load. Switching a few thousands, or a few hundreds of thousands, of those synchronously may do real damage to the power grid. If your more selfish the evil doer can wait till your out of town (data from the thermostat) and turn the heat to minimum or maximum so you come home to an expensive mess. 162.158.74.213 17:39, 14 March 2018 (UTC)
I’m going to give them an update they can’t refuse
Is it just me or is it strange that the older the device is the better the case? I just do not understand the graph and the explanation as it is now, does not make sense to me. In case it is just me that fails to understand it, then the explanation is still not good enough... Because: "Explain xkcd: It's 'cause you're dumb." :D --Kynde (talk) 19:26, 12 March 2018 (UTC)
- It seems to me that you need to look at the area on either side of the curve. So, if a device is 10 years old, the section on the "worst case" side of the curve is larger. Therefore, it is more likely that your device is to be compromised. --Detroitwilly (talk) 19:38, 12 March 2018 (UTC)
- I somewhat disagree. I don't think that it's a discrete best-case, worst-case only problem that's divided by the line, rather that it becomes so unlikely that there will be people protecting you, the best case scenario would be having your thing part of an organized crime. It's simple so unlikely that you're being protected, that having a hacked device is the best scenario. Perhaps there is some worse, unseen scenario that is so bad that having a hacked device is better in comparison. 172.68.211.244 20:12, 12 March 2018 (UTC)
- It's referring to how, the older the device gets, the less likely it is the manufacturer is still maintaining it and keeping it working.
- In that scenario, having your device be part of a botnet eventually becomes the best-case scenario, as the hackers would be providing the "support" and updates you need to keep the device working, as per the title text.
- The curve indicates that the older the device gets, the more likely it is it would be considered a best-case scenario for the device to be part of a botnet, for the aforementioned reasons. 162.158.126.76 06:46, 13 March 2018 (UTC)
- I must admit that nothing written here above or the new explanation helps me understand the curve or the legends in the graph. Also it seems people disagree so it is not just me ;-) To me it seems that it shows that the older the device is the better a case you are with. Maybe because you will have regular updates from the owners of the bot net, more so than from the company you bough it from even to begin with, and the dip is when they slow down the updates, at which point you are overtaken by the bot net and get's more updates. But it still doesn't really make sense... :D --Kynde (talk) 14:20, 14 March 2018 (UTC)
- I somewhat disagree. I don't think that it's a discrete best-case, worst-case only problem that's divided by the line, rather that it becomes so unlikely that there will be people protecting you, the best case scenario would be having your thing part of an organized crime. It's simple so unlikely that you're being protected, that having a hacked device is the best scenario. Perhaps there is some worse, unseen scenario that is so bad that having a hacked device is better in comparison. 172.68.211.244 20:12, 12 March 2018 (UTC)
In all honesty, being added to a botnet is not really a disadvantage for the average joe. 99.99% of all "undocumented administrators" have no interest in the user, only in the power and network speed of their device. So who cares if your "smart lightbulb" is mining bitcoins for the russian mafia? Average Joe certainly doesn't 172.68.51.106 08:35, 13 March 2018 (UTC)
I read this as Smart Home-Security, not Smart-Home Security. In other words, that it's talking about IOT home security cameras and other security devices, not just generic IOT stuff. This seems to explain the "rescued from peril" and "organized crime" parts a bit better. TheAnvil (talk) 16:05, 13 March 2018 (UTC)
Is this really about white hat hackers? It seems more like a commentary on the state of manufacturer security updates for Smart Devices. With a 50% chance that your software is already depreciated. With the title text suggesting that maybe organised crime might end up providing the updates. 108.162.238.101 02:45, 14 March 2018 (UTC)